LeasePak Roles and Users
Describes the various types of LeasePak and mPower users and how to set up their accounts and passwords.
Types of Users
Administrative Users
- Database Software Administrator
- Default
oracleorsybase. Performs installation and configuration functions for the database server software. You must create a separate Unix/Linux group to go with this user. Refer to the remainder of this document for instructions on creating accounts for LeasePak users. - DBMS Server Administrator
- Default
srvadm. Performs the functions of eithersysdba(for Oracle) orsa(for Sybase) to administrate the database server, individual databases/schemas, and users. Refer to the remainder of this document for instructions on creating accounts for LeasePak users./dd> - LeasePak Administrative User
- Although you can assign this role to the MSI release administrator (
msiadmin),msiadmincan no longer change its own environment (or the environment ofmsidba) by usingchange_env, so NetSol recommends creating a separate user, such aslpadmin. This user performs software administration tasks such as adding new LeasePak users into the Security [U0706] update, submitting batch files, running End of Period, and using programs from$uexe/lpautil.exe.exe. Set up thelpadminuser as part of the initial installation and configuration of LeasePak. You can also create a separate LeasePak administrative user for each environment, thereby avoiding the need forchange_env. Refer to the remainder of this document for instructions on creating accounts for LeasePak users. - MSI Database Administrator
- Default
msidba. Performs tasks and runs scripts related to the configuration and administration of LeasePak databases, includingdb_create,db_add_login, anddb_add_user. Refer to the remainder of this document for instructions on creating accounts for LeasePak users. - MSI Release Administrator
- Default
msiadmin. Performs tasks and runs scripts related to the configuration and administration of the LeasePak server software, including LeasePak queue manager configuration andsetup_new_env. Refer to the remainder of this document for instructions on creating accounts for LeasePak users.
General LeasePak Users
Also known as LeasePak client users. These are LeasePak users with client string passwords allowing them to log on the LeasePak client, but, in most cases, no access to the server or DBMS. They may have access to both LeasePak updates and reports, or LeasePak reports only. Level and type of privileges will depend on the individual user's assigned tasks and responsibilities. Refer to the remainder of this document for instructions on creating accounts for LeasePak users.
Partial Update LeasePak Users
Like general users, these have client string passwords for logging on the LeasePak client without having direct access to the server or DBMS. Unlike general users, their update capabilities are confined to Application Tracking and a few other related updates by marking the LeasePak Account Status as 'Partial Upd. User' on the Portfolio Security Tab of the Security [U0706] update. Refer to the remainder of this document for instructions on creating accounts for LeasePak users.
mPower Users
All mPower applications--ChannelIT, DocIT, LinkIT, and ServIT--require you to first set up the Web Services API (LinkIT) user.
LinkIT User
This is the account the Web Services API uses to log on LeasePak. Set up one API account, separate from any other users you set up for ChannelIT or ServIT, for use with all your mPower applications. You can also use the LeasePak Administrative User (lpadmin) for this purpose if you add access to the Application Tracking module to the lpadmin account (see step 2 below).
A LinkIT user cannot also be a ChannelIT or ServIT user.
To set up a LinkIT user:
- First, set up a typical LeasePak general/client user. Refer to the remainder of this document for instructions on creating accounts for LeasePak users. After setting up the account, note the user name and password.
- Add access to the Application Tracking module by giving the user a profile in Application User Profile [U0831].
- On the mPower server, after installing the mPower software ,
configure the
web.xmlfile (located in thempower/WEB-INFdirectory) with the LinkIT user name (theapiuid) and password (theapipwd). This sets up the LinkIT user.
ChannelIT Dealer Users
You cannot use the LinkIT user for a ChannelIT or ServIT user.
Typically a member of the lessor's dealer network authorized to begin the origination of new business in LeasePak. To set up a ChannelIT dealer user:
- First, set up a Vendor (Dealer) using the Vendor [U0201] update. This corresponds to the name and location of the specific dealer in your network.
- Then set up a typical LeasePak general/client user. Refer to the remainder of this document for instructions on creating accounts for LeasePak users.
- Add access to the Application Tracking module by giving the user a profile in Application User Profile [U0831]
- On the Portfolio Security Tab of the Security [U0706] update, restrict the user to the Vendor set up in step 1.
- On the same tab, make the user a partial update user by marking the LeasePak Account Status as 'Partial Upd. User'.
- On the Reports Tab of Security [U0706], check the box for (turn on) 'XML Reports'.
- Click OK to save the security setup changes. This sets up the ChannelIT dealer user.
ChannelIT Salesperson Users
You cannot use the LinkIT user for a ChannelIT or ServIT user.
These are Application Tracking users who may be logging on remotely or using ChannelIT as their interface to LeasePak. To set up a ChannelIT salesperson user:
- First, set up a typical LeasePak general/client user. Refer to the remainder of this document for instructions on creating accounts for LeasePak users.
- Add access to the Application Tracking module by giving the user a profile in Application User Profile [U0831]
- If the user will only be a ChannelIT user, you can mark the LeasePak Account Status (on the Portfolio Security Tab of the Security [U0706] update) 'Partial Upd. User'. If, however, the user will also access LeasePak through the standard client software, you must use the designation 'Regular User'.
- On the Reports Tab of Security [U0706], check the box for (turn on) 'XML Reports'.
- Click OK to save the security setup changes. This sets up the ChannelIT salesperson user.
DocIT Users
DocIT users are actually ChannelIT users, since DocIT is always used in conjunction with ChannelIT. Follow the instructions above for setting up ChannelIT users.
ServIT Users
You cannot use the LinkIT user for a ChannelIT or ServIT user.
These are customer end-users with authorization to view limited account and payment information in LeasePak and possibly make updates to address or other personal information. To set up a ServIT user:
- First, follow the instructions above for setting up a LinkIT user.
- On the mPower server, after installing the mPower software, use
vior other program to edit thecss_db.xmlfile (located in thempower/WEB-INFdirectory). Refer to the mPower server documentation for details.
User Accounts
Overview
The following table illustrates which accounts you will need to set up for the various types of users.
| User | Default | Default Group | Unix/Linux Account |
DBMS Account |
LeasePak Account |
|---|---|---|---|---|---|
| database software administrator | (oracle or sybase) | (oracle or sybase) | yes | ||
| DBMS server administrator | srvadm | N/A | (see below) | ||
| LeasePak administrative user | lpadmin | msi | yes | yes | yes |
| LeasePak client user(s) | (various) | msi | yes | yes | yes |
| MSI database administrator | msidba | msi | yes | ||
| MSI release administrator | msiadmin | msi | yes |
DBMS administrative user (srvadm)
Do not create a Unix/Linux or DBMS account for this user. The LeasePak server setup program prompts for a new user
name (default is srvadm) and password, then uses these to create either a login in Sybase and grant it
sa privileges, or create an Oracle schema (using a default tablespace) and grant it sysdba
privileges. Normally only the msiadmin and msidba users know the srvadm password.
LeasePak Environment Startup Files
The LeasePak environment files .lplogin and .lpprofile only need to be incorporated into the
startup files of users who perform LeasePak-related tasks requiring direct access to the LeasePak server. These users
typically include msiadmin and msidba, whose startup files should always point them to the administrative
environment (adm_*), and lpadmin, but can also include other users as
needed.
Passwords
LeasePak Client
When Leasepak administrative, updates, or reports users log on the LeasePak client, the password (called the client string) they use is passed through and translated into the actual three passwords required to connect to the LeasePak server--a network password, a server OS password, and a password for the DBMS. The algorithm translating the client string always produces the same output--that is, "string" always translates to "yihnx8" and "tjgui3." MSI does not recommend using the word "string" for an actual client string.
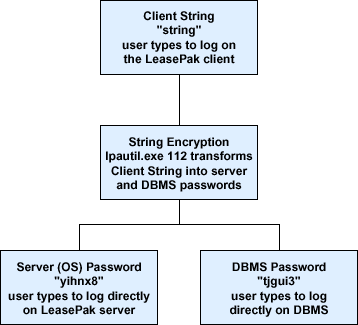
Users logging on the LeasePak Client only know their client string unless they are explicitly given the server or
DBMS password separately. Normally, only LeasePak administrative users (such as lpadmin) know their
passwords for logging on the LeasePak server and DBMS server.
Password Configuration
This password system depends on setting up the users' LeasePak server and DBMS accounts using passwords that match the translations of the client string. The following is an overview of the steps for adding a new LeasePak client user
- Select an initial user name and client string. This string must be between 6 and 8 characters in length. The LeasePak client user can change the client string (and the translated passwords with it) later through the LeasePak client Change Password option
- Use
$uexe/lpautil.exe 112to determine the translated server and DBMS server passwords based on the client string - Create server and DBMS server accounts for the LeasePak user with the correct translated passwords
- Add the user to the appropriate LeasePak database(s)/tablespace(s)
- Log on the LeasePak client as the LeasePak administrative user (
lpadmin) - Use the LeasePak Security [U0706] update to add the user to the LeasePak security table (
rsc).
Do not use $uexe/lpautil.exe 108 to add any user to the LeasePak security table other than the
LeasePak administrative user. The $uexe/lpautil.exe 108 function provides no control in how the user is added to
LeasePak security, and the LeasePak administrative user must still log on the LeasePak client in order to correctly
configure a user's security.
User Names
Create user names in compliance with your company's security guidelines. Use the same user name when setting up the server and DBMS accounts.
Client Strings
Create client strings in compliance with your company's security guidelines. Client strings must be 6 to 8 characters in length.
Translating Passwords
Use $uexe/lpautil.exe 112 to translate the client string
- Log on the LeasePak server as
msiadminorlpadminTerminal emulation: you must use one of the supported terminal types. Refer to System Requirements for more information.
- Type
$uexe/lpautil.exe 112and press Enter The terminal will promptThis Utility option may be used to translate a Client password into the equivalent Unix and SQL Server passwords. Do you wish to continue (Y/N)?
Type
yand press Enter. - The utility will prompt for the client string
Unix and SQL Server password translation utility Instructions: Enter the Client password. The equivalent Unix and SQL Server passwords will be displayed. Enter the Client string, <RETURN> to exit:
Type the selected client string and press Enter. If type
passwordas the client string, the terminal will displayClient string: password SQL Server string: rkqcguh4 Unix string: rrchglt1
MSI does not recommend using the word "password" as an actual client string.
- The utility will prompt for another client string
Enter the Client string, <RETURN> to exit:
Press Enter to exit the utility.
You can create a text file to translate several client strings at once
- Log on the LeasePak server as
msiadminorlpadmin. - In your home directory, use
cat,vi, or other means to create a text filepassword.iny passwd1 passwd2 passwd3 passwd4
The last line of the file must be a blank line (newline character).
- Run
$uexe/lpautil.exe 112with input and output files$uexe/lpautil.exe 112< password.in > password.out - Use
cat,vi, or other means to view the fileThis Utility option may be used to translate a Client password into the equivalent Unix and SQL Server passwords. Do you wish to continue (Y/N)? y Unix and SQL Server password translation utility Instructions: Enter the Client password. The equivalent Unix and SQL Server passwords will be displayed. Enter the Client string, <RETURN> to exit: Client string: passwd1 SQL Server string: kudejz2 Unix string: stpjvq0 Enter the Client string, <RETURN> to exit: Client string: passwd2 SQL Server string: aodmbd9 Unix string: drczoy0 Enter the Client string, <RETURN> to exit: Client string: passwd3 SQL Server string: qiduth2 Unix string: cjpvty4 Enter the Client string, <RETURN> to exit: Client string: passwd4 SQL Server string: kedahf9 Unix string: bfcfsq2
(etc.)
MSI does not recommend using any of the above client string examples as actual client strings.
Server Accounts
Follow the appropriate instructions for your OS platform to add a LeasePak user account with the translated
password. Make the LeasePak group msi the primary group for the user, and ensure that the user can
write to the $HOME directory. If you assign a user's UID number manually, do not use a number greater
than 32757. Contact your NetSol representative for more information.
Adding LeasePak users: make msi the group for all LeasePak users,
but do not add users to the msi line of the /etc/group file.
Having all LeasePak users listed on this line will cause fatal errors during the LeasePak installation.
Multiple concurrent versions: if you are running more than one version of LeasePak on the
same server, be sure to use the appropriate startup files (such as .lplogin and .lpprofile)
with the MSI release administrator for the version you are working in. NetSol strongly recommends that you set up separate,
version-specific MSI release administrator users for this situation.
DBMS Accounts
Use the LeasePak script db_add_login to create an account on your DBMS server
- Log on the server as
msidbaTerminal emulation: you must use one of the supported terminal types. Refer to System Requirements for more information.
- Run the
db_add_loginscriptdb_add_login dbms-type new-login-name [new-login-password [srvadm-password]]
where dbms-type is either
orafor Oracle orsybfor Sybase, new-login-name is the same user name as the server account, new-login-password is the corresponding translated password, and srvadm-password is the password for thesrvadmuser.
You can create a script to add several DBMS users at once
- Log on the LeasePak server as
msiadminorlpadmin. - In your home directory, use
cat,vi, or other means to create the filemy_add_logindb_add_login dbms-type msitest1 kudejz2 srvadm-password db_add_login dbms-type msitest2 aodmbd9 srvadm-password db_add_login dbms-type msitest3 qiduth2 srvadm-password db_add_login dbms-type msitest4 kedahf9 srvadm-password
- Run the script
- for Korn/Bourne/HP-UX Posix shell (
sh) users, typesh my_add_loginand press Enter - for C shell (
csh) users, typecsh -c my_add_loginand press Enter
MSI does not recommend using any of the above user names or passwords as actual user names and passwords.
- for Korn/Bourne/HP-UX Posix shell (
Database Permissions
Use the LeasePak script db_add_user to grant permissions to a specific LeasePak environment and database
- Log on the server as
msidbaTerminal emulation: you must use one of the supported terminal types. Refer to System Requirements for more information.
- Run the
db_add_userscriptdb_add_user environment-name legal-DBMS-user msi-access-group dbo-password
where environment-name is the specific LeasePak environment, legal-DBMS-user is the user's DBMS account user name, msi-access-group is either
msifor normal read/write permissions ormsirfor read-only permissions, and dbo-password is the password for thedboof the specific database (as specified duringdb_create.
You can create a script to add several DBMS users at once
- Log on the LeasePak server as
msiadminorlpadmin. - In your home directory, use
cat,vi, or other means to create the filemy_add_userdb_add_user environment-name msitest1 msi dbo-password db_add_user environment-name msitest2 msi dbo-password db_add_user environment-name msitest3 msir dbo-password db_add_user environment-name msitest4 msi dbo-password
The user msitest3 is a reports user and will have read-only permissions for this database.
- Run the script
- for Korn/Bourne/HP-UX Posix shell (
sh) users, typesh my_add_userand press Enter - for C shell (
csh) users, typecsh -c my_add_userand press Enter
MSI does not recommend using any of the above user names as actual user names.
- for Korn/Bourne/HP-UX Posix shell (
LeasePak Security Records
Do not use $uexe/lpautil.exe 108 to add any user to the LeasePak security table other than the
LeasePak administrative user. The $uexe/lpautil.exe 108 function provides no control in how the user is added to
LeasePak security, and the LeasePak administrative user must still log on the LeasePak client in order to correctly
configure a user's security.
Security
LeasePak Server
On the LeasePak server, the root user controls security by determining
- which users have server (OS) accounts
- which users are members of the LeasePak user group (
msi).
The users msiadmin and msidba control security by determining
- which users have DBMS accounts
- which environments/databases users have permissions for
- what type of database permissions users have (read/write
msior read-onlymsir) - which LeasePak client users have explicit access to their server and DBMS account passwords, as well as the various
dbopasswords and the password forsrvadm(rootmay also control this).
The following table illustrates typical password access for the various types of users:
| Explicit Password Access by Account or Type | |||||
|---|---|---|---|---|---|
| Client String | Server | DBMS | srvadm | dbo | |
| msiadmin | yes | ||||
| msidba | yes | yes | yes | yes | |
| lpadmin | yes | yes | yes | yes | |
| LP client user | yes | ||||
LeasePak Client
On the LeasePak client, The lpadmin user or other administrator controls the privileges of other users through the Security
[U0706] update. This update configures the security records for users within a specific LeasePak environment/database--that is, each
database in LeasePak contains its own distinct security table and set of records. An administrative user for one LeasePak
environment/database will not have access to any other unless msiadmin gives them access to the environment and
msidba grants them access to the database.
Once lpadmin sets a LeasePak client user up with an initial client string password, the user can change the client string
(and the corresponding translated passwords) by using Change Password in the LeasePak Options menu. Using Change Password
does not reveal the server or DBMS password to the LeasePak client user.
For more information about changing passwords on the LeasePak client, refer to the document LeasePak Basics. For more information about LeasePak client security, refer to the document Security [U0706].
LeasePak Documentation Suite
©
by NetSol Technologies Inc. All rights reserved.
The information contained in this document is the property of NetSol Technologies Inc. Use of the information contained herein is restricted. Conditions of use are subject to change without notice. NetSol Technologies Inc. assumes no liability for any inaccuracy that may appear in this document; the contents of this document do not constitute a promise or warranty. The software described in this document is furnished under license and may be used or copied only in accordance with the terms of said license. Unauthorized use, alteration, or reproduction of this document without the written consent of NetSol Technologies Inc. is prohibited.